According to a recent study by Positive Technologies, “As expected, the most successful social engineering technique is the use of a phishing link—27 percent of employees clicked it. Users are not picky when reading the link URL, sometimes clicking it without a second thought. When a user is prompted to download a file and then run it, every additional requested action raises more suspicions. In these cases, only 7 percent of employees were inattentive and fell for the bait.”
With phishing attacks, more steps create red flags—and that means it’s less likely employees will fall for the scam. But phishers are getting better and better at making emails look legitimate. And if scam emails look legitimate, many employees will fall for them.
If you don’t think phishing is a problem at your city, take your total number of employees and multiply that by 0.27. The answer is the total number of employees who are statistically likely to click on a phishing email. But remember it only takes one employee to be fooled for your city to become the latest victim of cyber criminals.
Training helps lessen that risk. In this post, we dissect the tactics scammers use in phishing emails. Your city employees should know about these tactics and receive regular training about them.

1. Convincing email subject lines
A recent TechRepublicarticle outlined 11 common email subject lines used to trick employees. Notice the pattern for how these subject lines are meant to get your attention and replicate an urgent notice from a legitimate source.
- Review or Quick Review
- Bank of [Bank Name]; New Notification
- Charity Donation for You
- FYI
- Action Required: Pay your seller account balance
- Unauthorize login attempt
- Your recent Chase payment notice to [name of employee]
- Important: (1) NEW message from [Bank Name]
- AMAZON: Your Order no #812-4623 might ARRIVED
- Wire Transfer
- Assist Urgently
Scammers are looking to get your attention so that you open their email, and they use compelling email subject lines to do it.
2. Convincing sender email address
Scammers have gotten good at spoofing email addresses from people. You may receive an email that looks suspicious (such as saying, “Click here!”), but you might trust the email because it looks like a friend, family member, or co-worker sent it. Their name appears along with their correct email address, so you logically think it’s from them.
So, how do you know whether it’s really from them? Look at other clues within the email. Does the message sound like something that person would send? Is it consistent with previous messages? If you have any doubt at all, call that person and ask if they sent it.
3. Convincing message
Here is where scammers often hit pay dirt. They become better and better at writing messages that seem legitimate. Let’s look at two tactics.
Classic deception
Scammers craft mass email messages that seem legitimate and trick you into clicking. For example, you might receive a message that says, “You have (1) new Amazon reward ready to claim.” If the email contains other Amazon-like messaging that seems legitimate and you’ve participated in similar rewards programs with companies, you may click on the link.
Business email compromise and spear phishing
Business email compromise takes a variety of forms but often involves scammers taking over an email account (by gaining access to a username and password), targeting specific people in your city by pretending to be the person whose account they took over, cultivating a targeted person over a period of time, and then enacting the scam.
According to the FBI, “[In] just about every [business email compromise] case, the scammers target employees with access to company finances and trick them into making wire transfers to bank accounts thought to belong to trusted partners—except the money ends up in accounts controlled by the criminals.”
Business email compromise is different than “spear phishing,” which involves the same tactics but instead relies on a spoofed email address rather than a compromised email account. The City of Paris, Kentucky experienced a spear phishing attack last year. If you want to learn more, we wrote a blog post interviewing the city clerk and analyzing the email.
4. Convincing look and feel
Another approach involves closely copying legitimate emails from a graphic design perspective. One way that people assess emails is by the look and feel. If it looks professional and sophisticated, it must be okay, right?
Take a look at this email. The scammer copies Google graphics fairly well so that, at a glance, it looks legitimate. The Google logo is correct, the blue button looks like Google buttons, and the messaging below the button looks professional.
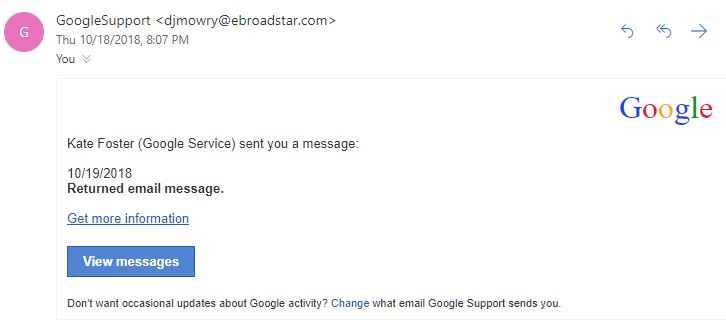
However, a few things should raise red flags:
- The email address does not look professional or related to Google at all.
- “GoogleSupport” is one word. That’s odd.
- What’s a “returned email message”? If you’ve used email for many years, you know that emails sometimes bounce back and you receive an automated message from the recipient. But you don’t get “returned email messages” with email.
- An organization like Google would send clear, professional, detailed messages during the rare times they contact you. This email raises more questions than it answers. It’s cryptic.
- Hovering over the button shows a URL that is suspicious and not related to Google at all.
Again, if you have any doubt whatsoever about an email, don’t click on anything. Instead, go directly to the company’s website or application. For example, if you had doubts about the message above, go directly to your Gmail account and see if any legitimate alerts or messages are waiting there.
5. Convincing attachments
Phishing scammers love it when you open attachments full of ransomware, malware, or viruses. To tempt you to open them, they use Word documents, PDFs, and zip files with normal business terminology like “contract,” “invoice,” “order,” etc. For example, look at the following message.
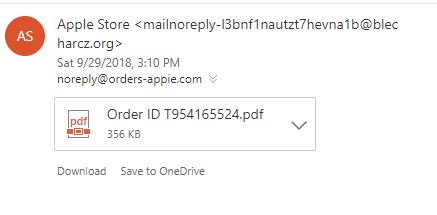
At a glance, you might just see “Apple” and “Order” and think, “Did I order something? Let me check the order.” You click on the PDF and…it’s not a PDF. Something starts downloading to your computer and suddenly you’ve got a ransomware virus infecting your city.
Do not, do not, do not click on suspicious attachments. In the email above, notice the strange email address and complete lack of information about the order. If you have doubt, ask the sender if they sent you a legitimate email with a file or document.
6. Convincing links and buttons
Scammers can sometimes spoof links and buttons. In some sophisticated phishing emails, a link can look legitimate but then redirect you to a malicious website that asks you for a username/password, financial information, or information that helps a hacker take over an account. Other links may initiate or get you to download malware, ransomware, or a virus.
Unless you are absolutely certain an email comes from a trusted sender, don’t click on links from an email. For example, even if you think an email from your bank is legitimate, be safe by going directly to the bank’s website.
By understanding the different components of a phishing email, you can better spot the signs of a scam. This post should also highlight the importance of cybersecurity training for city employees. Addressing topics like phishing helps city employees stay aware and guarded against cyberattacks—lessening your risk of human error and lowering your liability.
Need help with cybersecurity training? Reach out to us today.





