The word “Maturity” is part of the Cybersecurity Maturity Model Certification for a reason. Essentially, the Department of Defense wants their chain of suppliers to “grow up” in their security. When companies act like “grown-ups” in the way that they manage cyber risk, they’re a lot more serious about their responsibilities and they’re accountable for the outcome.
Once you’ve gone through a CMMC Gap Analysis and you have a Remediation Plan in hand, the actions that you’ll need to take to increase your security maturity may fall into different categories. Some of the actions will involve non-technical layers of security, such as implementing and enforcing policies that guide access to data. Others will involve IT best practices, such as keeping hardware and software up to date. Still, others will have to do with modifying the way that your IT systems are set up.
All of these security tactics will move you towards a basic level of maturity.
The fourth category of security controls that you’ll find on your CMMC Remediation Plan involves technology solutions, and you may find that there are three advanced solutions that you don’t have right now that you absolutely need.
Because you’ve never used them before, you might at first think that these software tools are security overkill. But they’re not.
The baseline for security has changed and if you want to not only attain CMMC compliance but keep up with evolving cyber risks, you should be considering these solutions for protecting your whole network, not just the part that handles Controlled Unclassified Information (CUI).
Three CMMC Remediation Plan Must-Haves
1. Multi-Factor Authentication (MFA)
MFA is an identity management solution that puts double doors between your network and outsiders. It requires that users perform a second action to prove that they are the “authentic” account holder. Imagine that a cyber criminal cracks an employee's password. With MFA, they still have another barrier to get around.
These additional barriers could be provided in a mobile app or a fob that requires another action. Unfortunately, many employees see MFA as an inconvenience because it forces them to add a step to their workflow. Security trumps convenience, however, when it comes to proving to CMMC auditors that your account access protocols measure up to the security maturity level that you need to have to keep your DoD contracts.
Related: Learn more about MFA and how to pick the right solution
2. Endpoint Detection and Response (EDR)
EDR is a technology tool that uses Artificial Intelligence (AI) to learn about the traffic on your network so that it can respond and alert you when something abnormal happens.
While EDR doesn't replace traditional firewalls, it makes it possible not just to block intruders but to notify you about the suspicious activity so that you can stop potential intrusions before they turn into full-blown attacks.
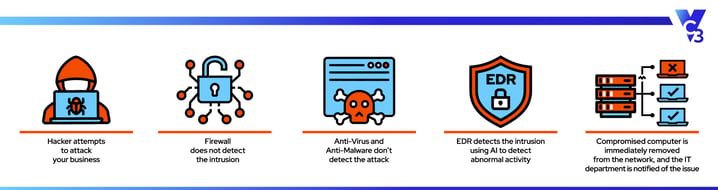
The need for EDR has arisen because more and more cyber attackers are getting into IT systems through unknown vulnerabilities. Once in, they’re lurking around looking for the biggest payoff, which might be a phishing scam using you or your customers as bait or getting access to other networks where there might be an even bigger fish to reel in.
Related: 17 Foundational Cyber Security Measures Southern California Businesses Need
3. Security Information and Event Management (SIEM)
SIEM is a software tool that gathers and retains logs documenting network security. Essentially, it’s the breadcrumbs that forensic experts can follow to find out why a cyber attack happened. It’s also the data that security specialists need in order to monitor your systems and make sure that you’re responsive to changing conditions.
Of all of the technology solutions that companies need in order to comply with CMMC, this is the one that is the most novel to executives. The need for extensive cyber documentation raises questions that can only be answered by getting a better understanding of cyber risk, and why becoming a better manager of that risk is imperative to business success. Once you know the risks, it makes a lot of sense to prioritize prevention and response over crisis management.
Related: Get the Executive Guide to Cyber Security and learn how to be a better manager of cyber risks
Remediation Plan to Successful CMMC Compliance
Here at VC3, we’re committed to helping companies in the DoD supply chain move down a path that leads to successful CMMC compliance. That’s why we’ve invested in Registered Practitioner training for our CMMC consultants.
Our CMMC experts are here to walk you through each step of the CMMC compliance process, from facilitating a Gap Analysis to helping you prepare for your audit. Learn more about how our Registered Practitioners work with companies like yours.





