
VC3
Filter by

Blog
|
5 min read
Industry Specific Managed Service Needs for the Insurance Industry
These days, every industry and every sector needs to be up to speed with IT. Technological innovations across the board ...
Read More
Blog
|
< 1 min read
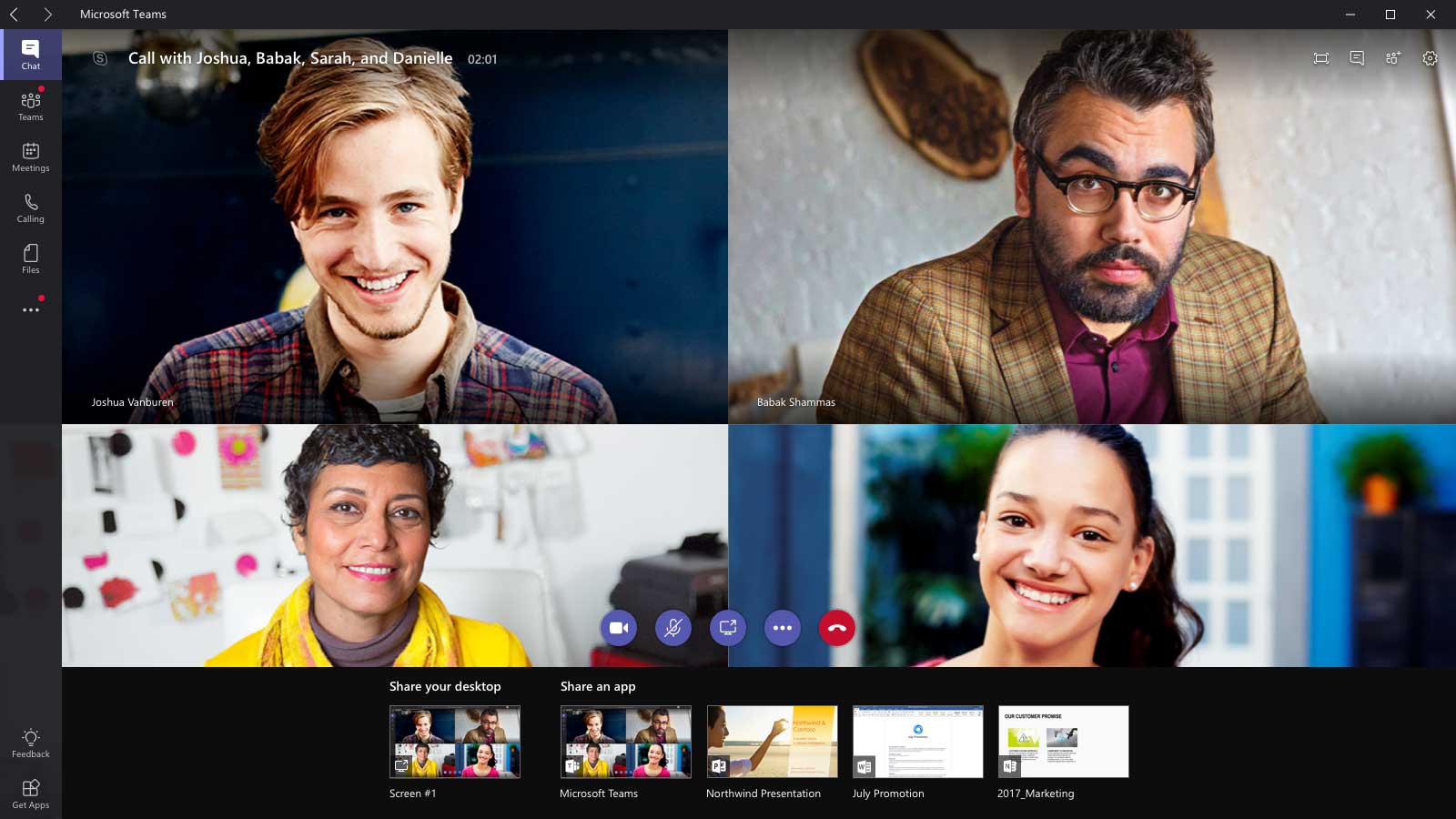
Setting Up a Conference Call with Microsoft Teams
As more employees, educators, and students work remotely in response to the spread of COVID-19, staying connected is mor...
Read More

Blog
|
4 min read
Industry Specific Managed Service Needs for the Legal Industry
Technological advances and innovations in the way we work are everywhere and are having a huge impact on every sector. A...
Read More

Blog
|
2 min read
How to Use Microsoft Find Time and Scheduling Assistant
I love efficiency and hate wasting time while waiting for peoples responses. When I discovered Outlooks Scheduling Ass...
Read More

Blog
|
4 min read
5 Data Backup Statistics That Should Concern Municipalities
Most municipalities would admit they need to back up their data. Thankfully, we find that municipalities usually have so...
Read More

Blog
|
3 min read
Email Vigilance Critical to Combat Phishing Attacks
Start by hovering over the link in the email. When you hover your mouse over a link (but dont click on it), it brings u...
Read More