The biggest cybersecurity threat to your organization is unprepared employees.
What do I mean? Regardless of where your organization is in its cybersecurity journey, one thing continues to be abundantly clear. Your employees must be adequately prepared to identify phishing attacks and sound the appropriate alarm. A cybersecurity firm found that 90% of data breaches are caused by human error. And it's the organization's responsibility to provide that training on a regular basis. The good news - employee awareness training doesn't have to cost an arm and a leg.
Hackers often take advantage of a current crisis like COVID-19 or other newsworthy events. Google’s Threat Analysis Group has blocked 18 million COVID-19 themed malware and phishing emails per day. While tech tools play a key role in preventing phishing attacks, it’s more important than ever that your employees are prepared and trained.
To fully appreciate the risks, we must first understand the data.
Phishing attacks are the most successful...
95% of successful cyber-attacks start with a phishing scam
More of these attacks are happening right now...
350% increase in phishing attempts according to Google since quarantine began
The financial impact is costly...
$1.1 million is the average cost of a cyber attack
And the long term effects on your reputation are damaging.
43% of attacked organizations report a negative customer impact and a loss of reputation
This means the most dangerous attack is being attempted more often which can result in major financial impact and loss of reputation for those attacked. The next two questions you must be asking yourself are:
- What can I do right now to better protect my organization?
- What do I need to do in the long term to become better prepared?
Let's tackle the first question. Now that phishing has our attention, we need to understand how to train ourselves and employees.
Let’s learn from a recent phishing example we caught at VC3 to make things more concrete.
This phishing attack was targeted at our CEO and looked like a folder share from SharePoint Online. It's one of the better-disguised messages we've seen. We’ll examine a real folder share and the phish side-by-side so you can see how tricky these can get and what to look for.
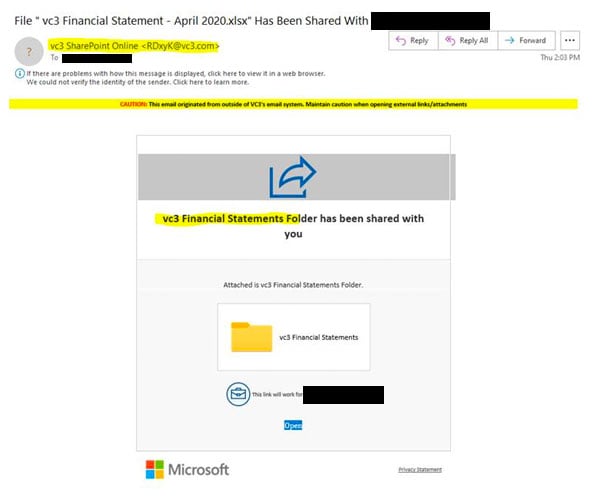
The phishing Attack example:
Indicators that it’s malicious:
- Note the “External Email” banner at the top of the message. VC3 uses a product to identify messages coming from outside the organization, so it makes it easy to spot that this did not come from our SharePoint site.
- It looks like it comes from VC3 SharePoint Online rather than the user that created the share.
- The statement at the top does not contain the user's name.
- The link is not to our internal SharePoint site.
- The Privacy Statement does not link to Microsoft.
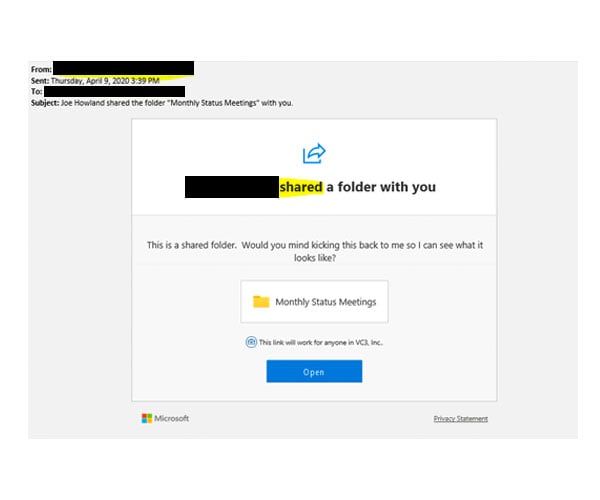
The legitimate SharePoint Folder share:
Indicators that it's legitimate:
- The email comes from the person that created the share and that person’s name is listed at the top of the message.
- The hyperlink contains VC3's intranet URL and that should be clear in the email.
- The “External Email” banner is missing because this came from within VC3
- The Privacy Statement Link at the bottom goes to Microsoft.com.
Long Term Answer
You need an employee awareness training program. There are plenty of strong options and it won't be a major investment. However, because there are so many options and it does require time to set up and manage, you also need a long-term cybersecurity partner. Cybersecurity is a journey, not a destination. Phishing attacks and many other cyber-attacks change and evolve, so it's important to have a partner who is aware of the evolving landscape to make sound recommendations.
Phishing Signs Guide [Free Download]
Want a more comprehensive guide to share with your employees? Fill out the form below to download a social engineering red flags email tip sheet from our employee awareness partner and industry leader, KnowBe4.





