Filter by
Guides
|
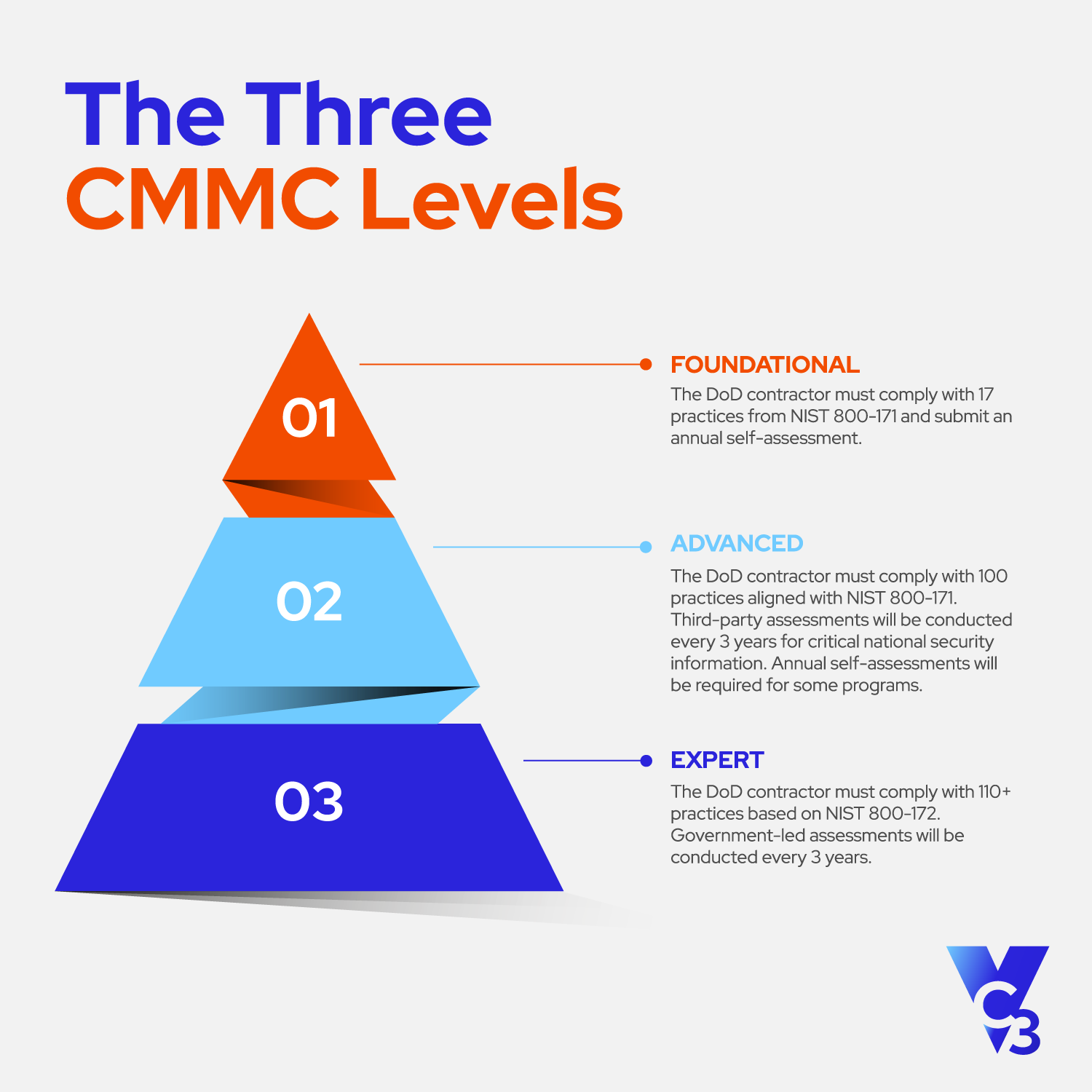
CMMC 2.0 Compliance Explained
Learn how the DoD supply chain will communicate and verify cybersecurity stature, what CMMC 2.0 means for Southern Calif...
Read More

Guides
|
Cybersecurity 101
Read this cybersecurity guide to learn why cyber criminals are targeting your business, the tactics they are using and w...
Read More

Guides
|
Data Backup, Disaster Recovery, & Business Continuity
It only takes one security breach, unexpected disaster, or an accidental “Delete” at the wrong time to make you REALLY r...
Read More

Guides
|
Flat Rate Managed IT Services and Support
Organizations rely on managed IT services to get better business results. Lower monthly IT costs and better IT services....
Read More

Blog
|
6 Min Read
Checklist for a Successful Transition from Windows 10 to Windows 11
We provide a checklist for a successful transition from Windows 10 to Windows 11—and some of the many things you will ne...
Read More

Blog
|
4 Min Read
Windows 11 Upgrade: What Are My Options?
The right Windows 11 upgrade path depends on your organization's size, complexity, and specific needs.
Read More
