Filter by

Blog
|
4 Min Read
How Much Does HaaS Cost?
Understand the costs of HaaS and the additional advantages it brings, such as freeing up capital and improving operation...
Read More
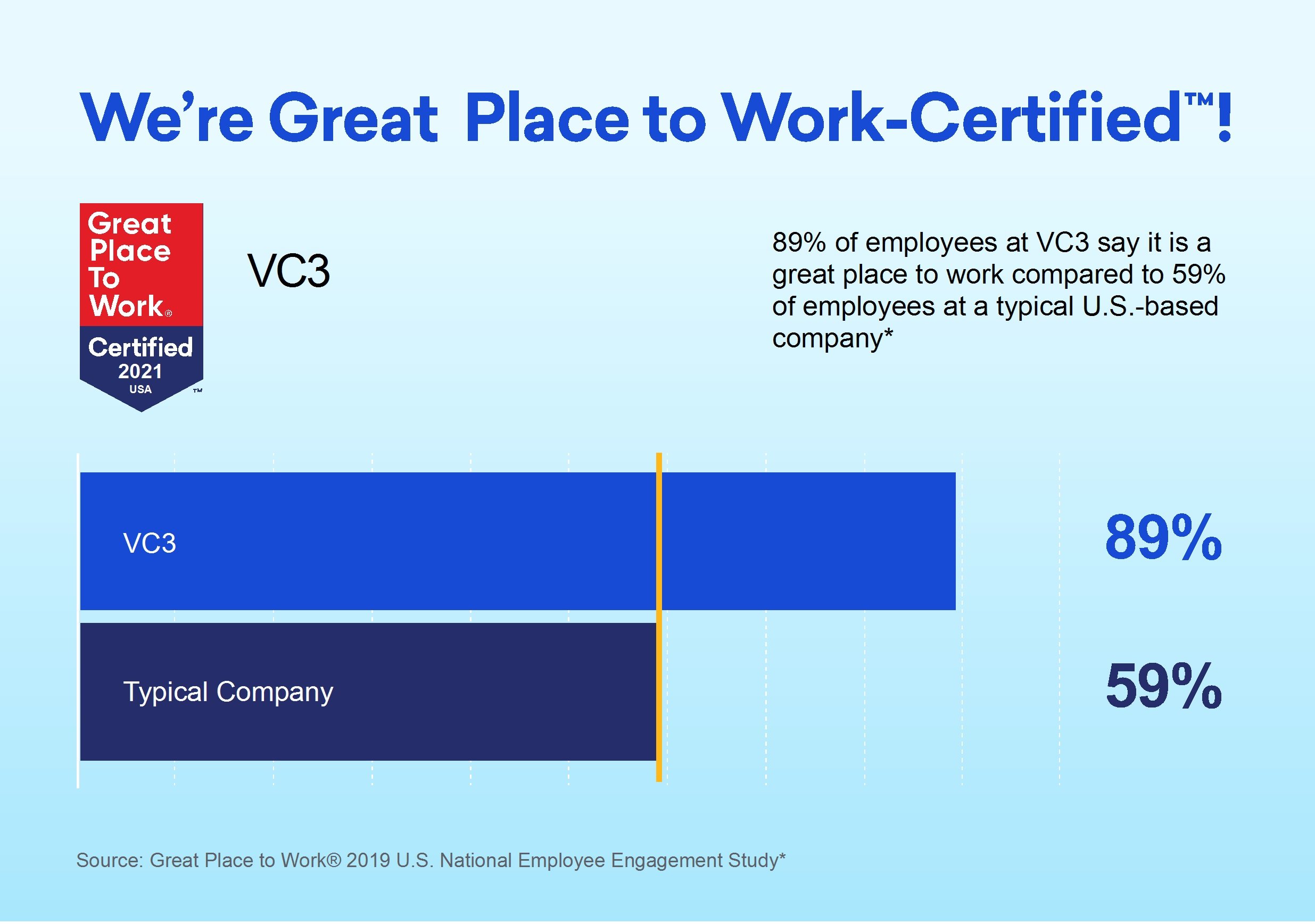
News
|
2 Min Read
VC3 Earns 2024 Great Place To Work Certification™
VC3, a leading managed IT and cybersecurity services provider, is proud to be Certified™ by Great Place To Work® for the...
Read More

Blog
|
3 Min Read
Still Relying on Antivirus? It’s No Longer Enough.
As cyber threats become increasingly sophisticated and frequent, it's essential for organizations to stay current with t...
Read More

Blog
|
4 Min Read
A Non-Technical Guide to Microsoft’s New MFA Policies—And How They Affect Y...
Microsoft has introduced three new Multi-Factor Authentication (MFA) conditional access policies to enhance security for...
Read More

Blog
|
5 Min Read
Introduction to Copilot for Microsoft 365
Learn how you can leverage Copilot—an AI tool that can be used within common applications such as Microsoft Word or Exce...
Read More

Blog
|
5 Min Read
Managed IT Services Cost & Pricing Guide: How Much Does Managed IT Services...
The price range for managed IT services runs from $99 to $250/user/month. Where your organization stands depends on the ...
Read More
