Far too often, small and medium-sized businesses tend to think that they’re not on a hacker’s radar or that a firewall and antivirus will keep them 100% protected against a breach.
But that’s not the case.
Cybercriminals steal whatever data they can and often use the compromised network to launch further attacks after penetrating your system or for extortion to sell your data back to you (or the highest bidder). That makes a business of ANY size a prime target.
Bad actors actively target network endpoints such as servers, desktops, and laptops; anything with a user operating system. With an average IT department managing hundreds (if not thousands) of endpoints, hackers have a field day with undersecured networks.
That’s where Endpoint Detection & Response (EDR) technology comes in.
Endpoint Detection and Response (EDR) Defined
Endpoint Detection and Response is a network security tool that continuously monitors your network’s endpoints in real-time to detect a breach the moment it happens.
EDR is considered a cybersecurity detection tool, not a prevention tool, but it takes corrective measures to isolate the threat and minimize loss and damage.
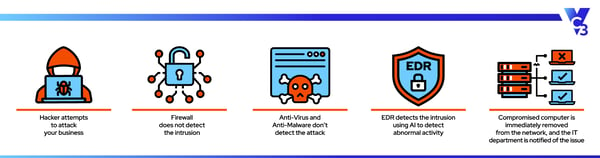
An EDR security system has four primary functions:
- Monitor, identify and collect suspicious data from endpoints.
- Analyze the data to identify possible threat patterns.
- Automated threat response – EDR swoops in automatically to contain or remove any identified threats and notifies the security team.
- Investigate identified threats and identify suspicious activities.
In the cybersecurity landscape these days, we see that with advancements in cybercrime tactics, detection is where small and midsize businesses need to invest.
How Does EDR Technology Work?
1. Establish a Baseline for What’s Normal
EDR technology uses intelligent algorithms to study and record user behavior while they are logged into your network. It then establishes parameters of what’s considered “normal behavior” for each user.
Having a read on each user’s “normal behavior” enables the system to establish a baseline. As a result, an EDR can zero in on odd or malicious behavior the moment it happens.
2. Monitor and Analyze Activity
When something outside of the “normal behavior” pops up, the abnormal activities will trigger the EDR solution to monitor and investigate the data for malicious actions in real time. An analysis of the data confirms if the threat is real or not.
3. Threat Tracking
When it detects a threat, the EDR tracks and follows the path of attack right to the vulnerable endpoint. The algorithm then collates and classifies the data into specific categories known as Malicious Operations.
4. Notification and Response Steps
The EDR will immediately notify your IT team if your system is under attack, giving you actionable response steps. It’ll even make forensic recommendations to help combat the threat.
Given its advanced algorithm, EDR monitors for stealth attacks, including malicious scripts, fileless malware, and stolen user credentials.
5. Ongoing Analysis to Find Your Weak Links
EDR technology also analyzes attacks to learn the tactics hackers used to penetrate your network. It also detects the paths they used to learn about your network so you can eliminate the weak links.
How Does EDR Compare to Other Security Measures?
EDR technology’s claim to fame is its incredible response time. The system automatically tracks and reveals the point of breach, its path, and its actions. With this information, your security team saves on post-breach time and effort to contain the breach quickly and effectively, getting you back in business more quickly.
Traditional security methods take longer to investigate, and time is not on your side when it comes to a cyberattack. A couple of minutes is all an attacker needs to breach your whole network, and the immediate response from an EDR solution can prevent that from happening in the first place.
EDR also provides the documentation your insurance company may require in the event that you need to file a claim. As a result, it may also reduce your cybersecurity insurance premiums.
Do I Need EDR and Antivirus?
Antivirus as a standalone service is simply no longer effective as a security tool. Many modern endpoint security solutions integrate features of both EDR and antivirus to offer comprehensive protection.
EDR solutions excel at detecting and responding to all threats—whether known or unknown—using behavioral analysis, threat hunting, and real-time monitoring to identify suspicious activities.
Designed for incident response, EDR offers insights into the nature of an attack and the scope of compromise, which facilitates quick remediation. This makes EDR more effective than antivirus against new and evolving threats.
Some cyberattacks, such as zero-day exploits and fileless malware, leave no signatures and make it impossible to detect an attack without an EDR solution. With antivirus now subsumed under EDR, you really just need EDR today.
Cybersecurity Protections for Small and Midsize Businesses
The cybersecurity landscape changes by the day, and having a team of trained cybersecurity professionals on your side is becoming increasingly more critical.
If you’re not sure if your business has adequate measures in place to detect and prevent cyberattacks, contact us today. Many business leaders are surprised at what the results show. Often, the remediation actions aren’t overly complicated or costly, and a few simple changes could save you hundreds of thousands of dollars (and help you sleep better at night).





