Antivirus software used to be as common as having a lock on your front door, serving as the primary defense for anyone looking to protect their IT network against cyber threats. However, just as physical security measures have evolved to counteract smarter threats, cybersecurity strategies have had to adapt to address new, more sophisticated dangers.
Today, cyber intruders can often bypass traditional antivirus protections with disturbing ease, prompting the need for more advanced methods of detection and response.
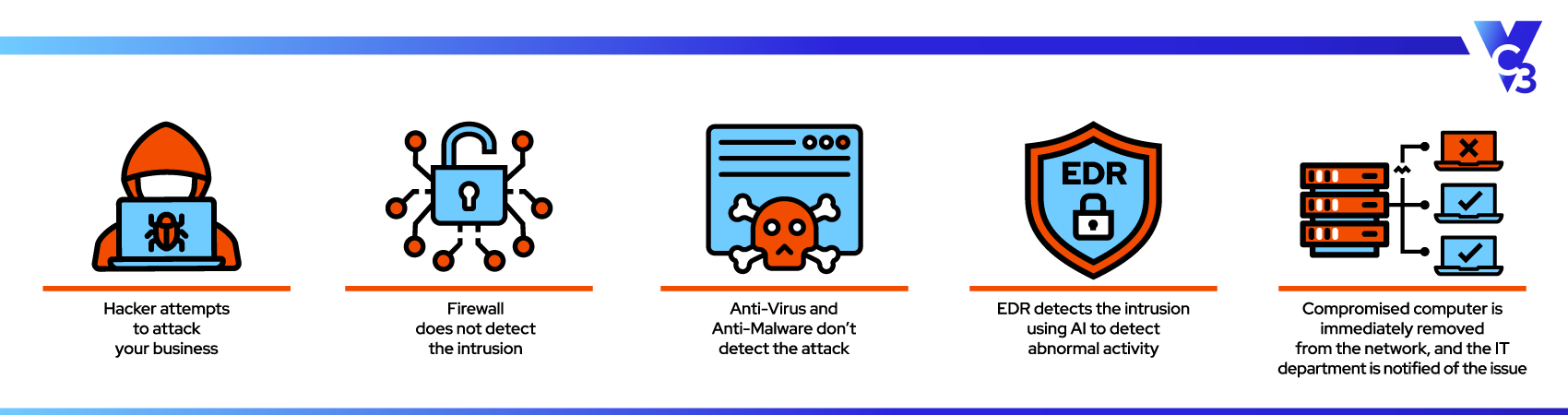
Endpoint Detection and Response, or EDR, works like a vigilant security camera that catches intruders in the act of entering a building after picking a lock. Adding security cameras doesn’t mean you get rid of the locks. Similarly, adding EDR doesn’t mean antivirus protection goes away. EDR includes the same functions as antivirus but also detects and actively responds to cyber threats in real-time.
As we’ll see, relying solely on antivirus leaves organizations vulnerable to a wide range of preventable risks. It’s simply no longer enough.
Antivirus Always Plays Catch Up
Antivirus software has traditionally served as a first line of defense to keep IT systems safe. It works by scanning files, email attachments, website URLs, internet downloads, and external devices on computers or networks. The software checks these items against its database of known threats. If it finds a match—essentially a digital “fingerprint” of malicious code from any of these sources—it blocks or quarantines the item.
The downside of this approach is that it’s inherently reactive, not proactive. The antivirus database is constantly updated but it can only include previously identified threats. New threats can slip by until they're eventually added to the database and updated in the antivirus software. But there’s always a period of time when new threats are undetectable by antivirus.
Endpoint Detection and Response (EDR) bridges this gap. While it will always be vital to protect IT systems against known threats, EDR can identify unknown threats—from zero-day vulnerabilities to anomalous behavior such as unauthorized access to sensitive files or unusual transfers of data at strange times.
EDR Looks for Threats and Takes Them Down
EDR systems are designed to go beyond the capabilities of traditional antivirus by continuously monitoring and analyzing data on endpoints—such as workstations and servers—to look for suspicious activity. This means that even if there’s a digital signal that doesn't match anything in the database of known threats, the unusual behavior can still be flagged for further investigation.
EDR works dynamically, actively hunting for signals of potential issues rather than waiting to match threats after they're already identified. The tool has become a cybersecurity best practice because of its proactive capabilities to learn and adapt to new cybercriminal tactics. This means organizations are not only prepared to face the threats of today but also equipped to anticipate and mitigate emerging threats.
Two main functions that set EDR apart from antivirus are its ability to look for threats and then to respond after it finds them.
- Advanced Threat Detection: By gathering and analyzing vast amounts of data from every endpoint, EDR systems can uncover complex threat patterns, including fileless malware. This in-depth analysis of system behavior can identify potential threats based on irregular patterns, offering protection against zero-day exploits—attacks that take advantage of security vulnerabilities before they’re patched.
- Real-time Response and Mitigation: When suspicious activity is detected, EDR isolates the endpoint from the network, preventing the spread of the threat. If necessary, security teams can roll back the endpoint to a previous (pre-infected) state, and the tool gives them information to successfully hunt down and extinguish the threat throughout other endpoints within the organization. This powerful feature minimizes disruption by immediately detecting and responding to threats.
The threat detection and response mechanisms of EDR sound impressive, but what does it look like in action? Does EDR really make that much of a difference in minimizing cyber threats?
EDR at Work
Consider this common scenario: an employee unknowingly clicks on an email embedded with fileless malware, a sophisticated form of ransomware that traditional antivirus cannot detect.
Without EDR: The ransomware is successfully installed on the employee’s device. At first, nothing looks amiss as the malware begins to explore and exploit the network unnoticed. Eventually, after infecting several systems and potentially gaining access to sensitive data for hours or even days, the antivirus registers the ransomware's “fingerprint” in the database and attempts to start the cleanup process. By then, the damage has been done.
With EDR: As soon as that same employee clicks on the email, the EDR tool picks up on the unusual activity. EDR isolates the device from the network, automatically cutting off the ransomware's ability to spread while sending an alert to the system administrator. The ransomware is remediated by the IT team and the immediate risk is neutralized. EDR’s interconnectedness with other security tools also keeps the administrator informed about the attack, making sure all other devices are safe.
The difference is clear. A sole reliance on antivirus solutions puts organizations at unnecessary risk. Even when antivirus solutions eventually detect threats, the delay often gives cybercriminals enough time to extract or manipulate data. With EDR, attacks can be stopped in their tracks before they cause any significant damage.
A Growing Necessity for Cyber Insurance
EDR's holistic and interconnected approach to cybersecurity is increasingly viewed as indispensable by cyber insurance carriers. Organizations without EDR are not just at a higher risk of security breaches but also face potential challenges in financial stability and long-term viability.
Today, incorporating EDR into a cybersecurity strategy is not just advisable. It's becoming critical for lowering cyber risk and increasing overall security readiness.
When cyber insurers categorize EDR as a must-have for policy qualification, it's a strong indicator of the application's essential role in modern cybersecurity defenses. Gone are the days when traditional antivirus solutions were sufficient. Today's cyber attackers are smarter and more devious, employing ransomware, misusing credentials, and exploiting zero-day vulnerabilities, often evading detection for prolonged periods of time.
EDR sets itself apart by offering advanced capabilities that go well beyond the confines of conventional defenses. Its strength lies in continuous monitoring for anomaly detection, in-depth incident analysis, and rapid response to threats—features that have made it a pillar in cyber insurance prerequisites.
The Value of Managed IT Services in Navigating Cybersecurity Trends
As cyber threats become increasingly sophisticated and frequent, it's essential for organizations to stay current with the latest cybersecurity trends and protective technologies. The inadequacies of traditional antivirus are glaringly evident. Transitioning to EDR is no mere upgrade but a necessary leap into the future of cybersecurity.
Here at VC3, we guide clients through the complexities of cybersecurity, ensuring they’re not left vulnerable to evolving threats and that they're fully leveraging innovations like EDR. By partnering with a provider who stays on the forefront of cybersecurity trends, our clients can focus on their core operations, secure in the knowledge that their IT systems are resilient and ready to face whatever challenges come next.






